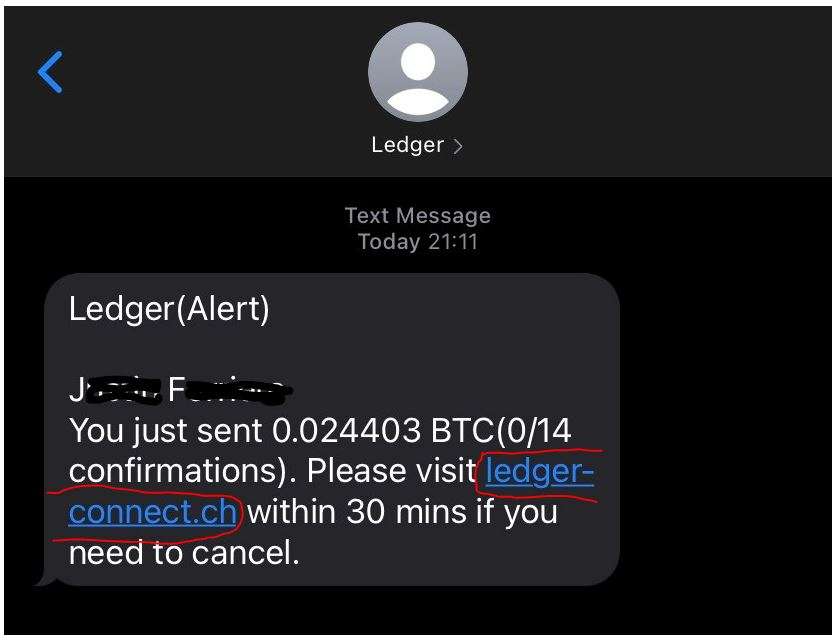
Oracle OCI Data Transfer Service – A journey from Kestenholz/Jurasüdfuss/ Switzerland to Frankfurt and back – martinberger.com
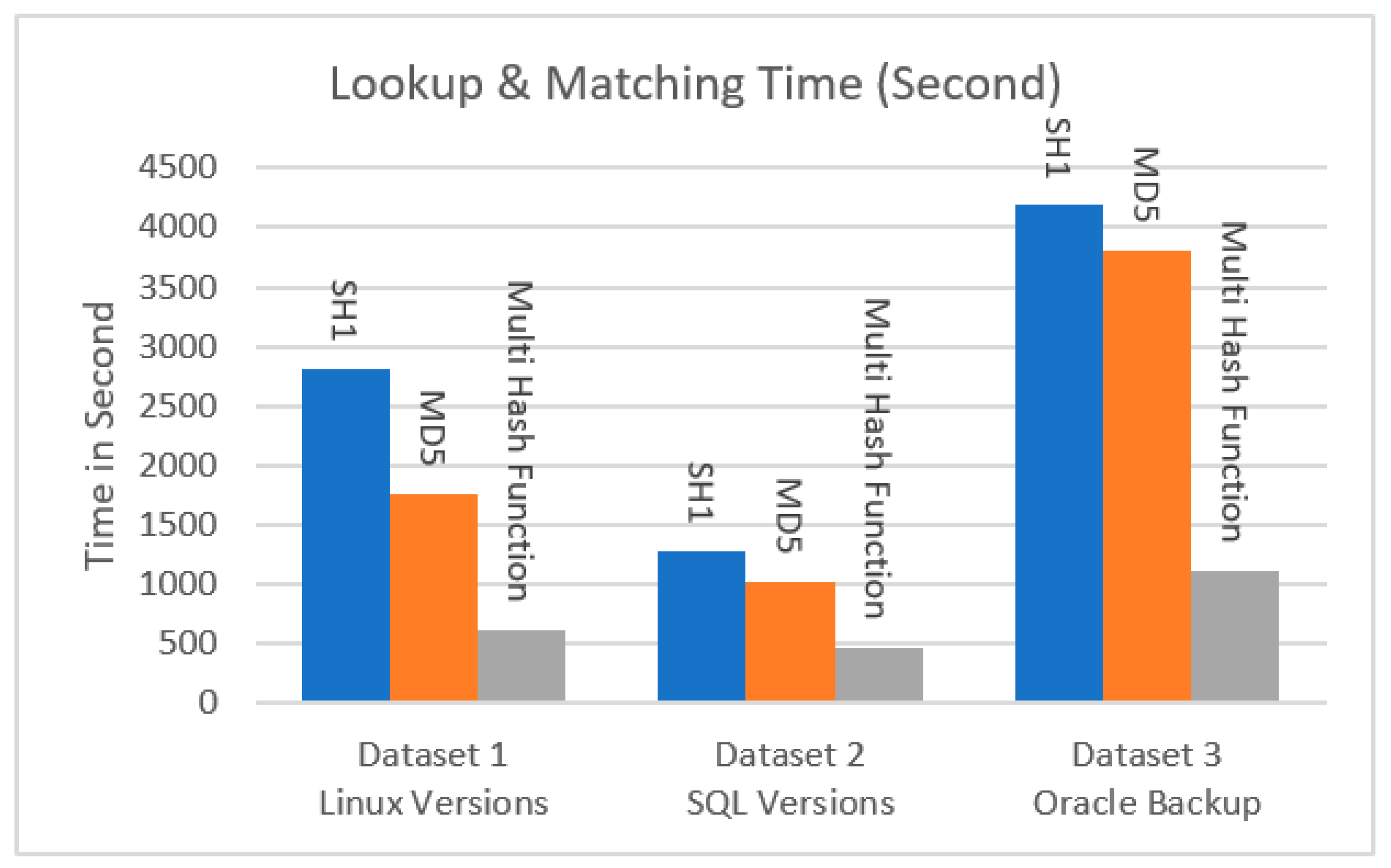
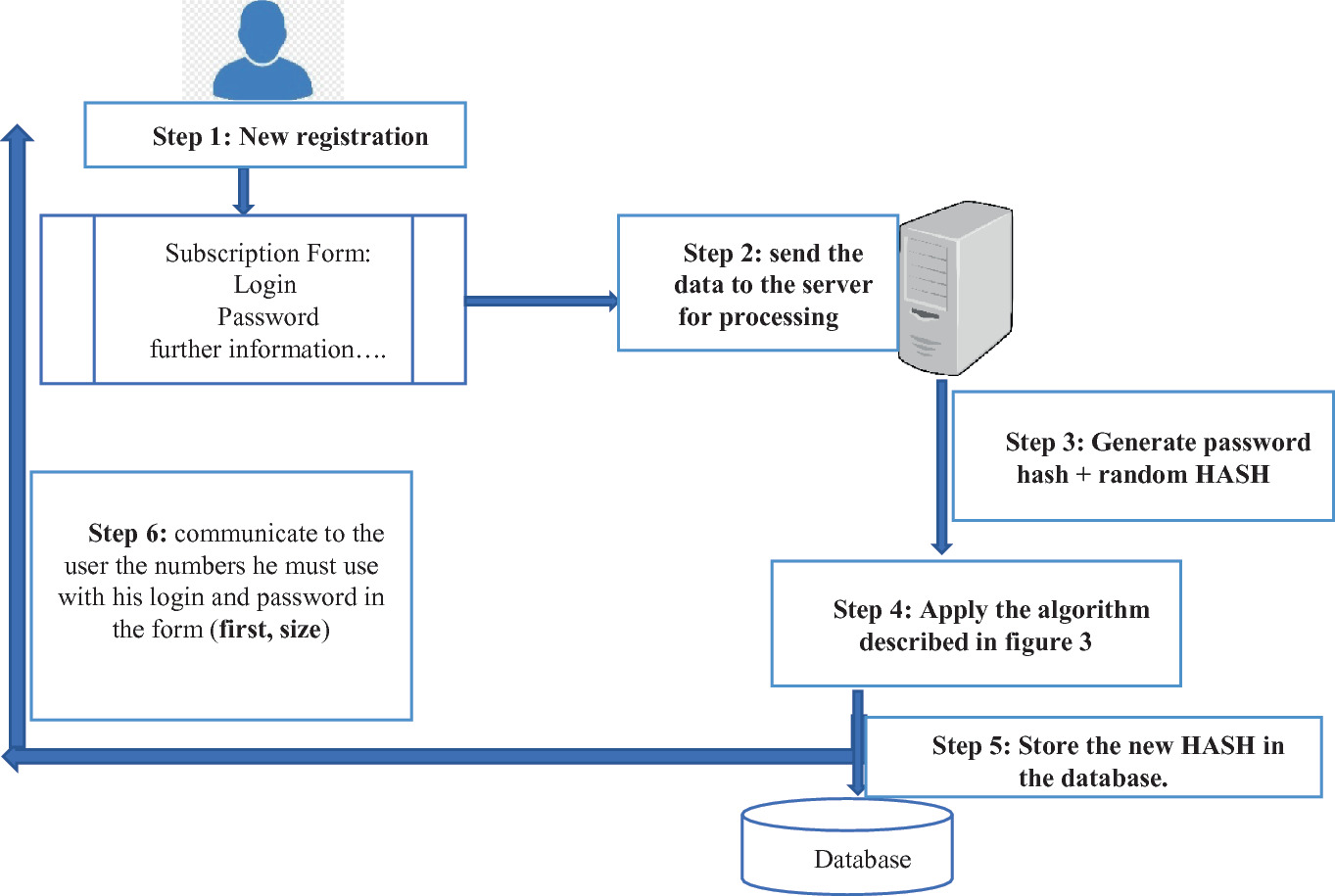
Symmetry | Free Full-Text | Fingerprint-Based Data Deduplication Using a Mathematical Bounded Linear Hash Function | HTML
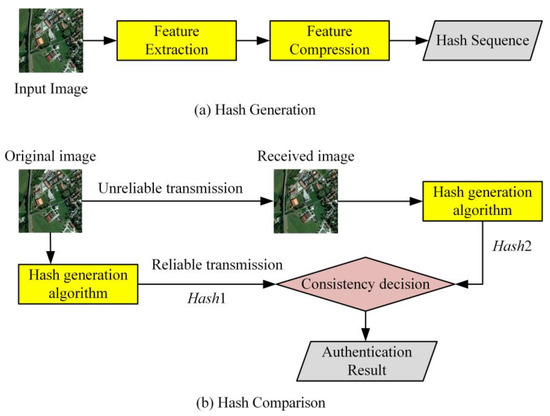
IJGI | Free Full-Text | High-Resolution Remote Sensing Image Integrity Authentication Method Considering Both Global and Local Features | HTML

Oracle OCI Data Transfer Service – A journey from Kestenholz/Jurasüdfuss/ Switzerland to Frankfurt and back – martinberger.com

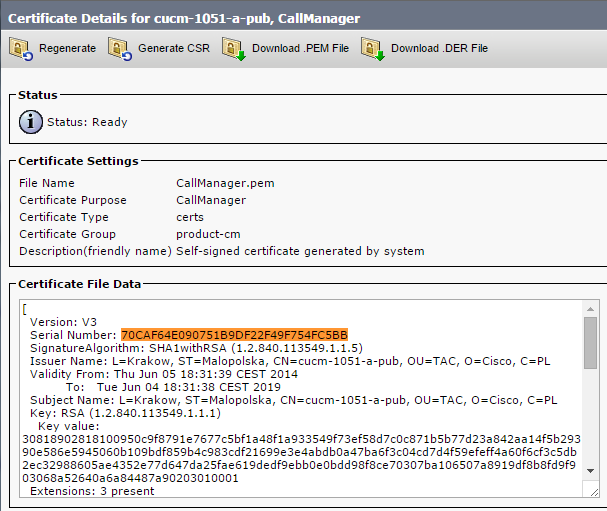
PPT - MD5 Considered Harmful Today Creating a rogue CA certificate PowerPoint Presentation - ID:201873

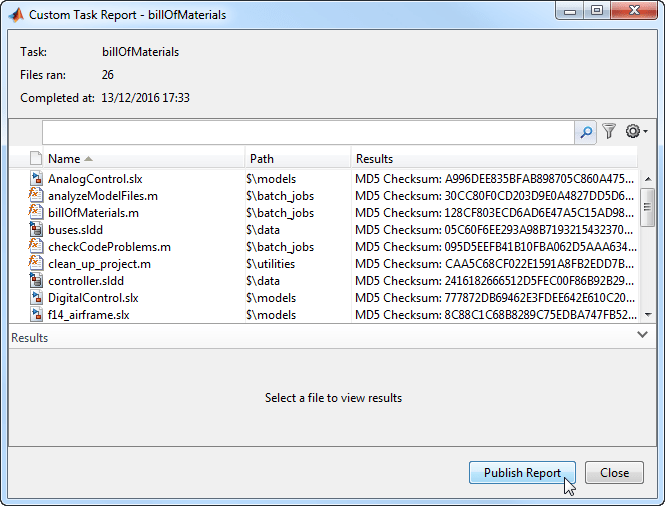
STM32F756ZG - High-performance and DSP with FPU, Arm Cortex-M7 MCU with 1 Mbyte of Flash memory, 216 MHz CPU, Art Accelerator, L1 cache, HW crypto, SDRAM, TFT - STMicroelectronics