
On the designing a secure biometric-based remote patient authentication scheme for mobile healthcare environments | SpringerLink

The results using 'verification claim' procedure in Scyther tool (see... | Download Scientific Diagram
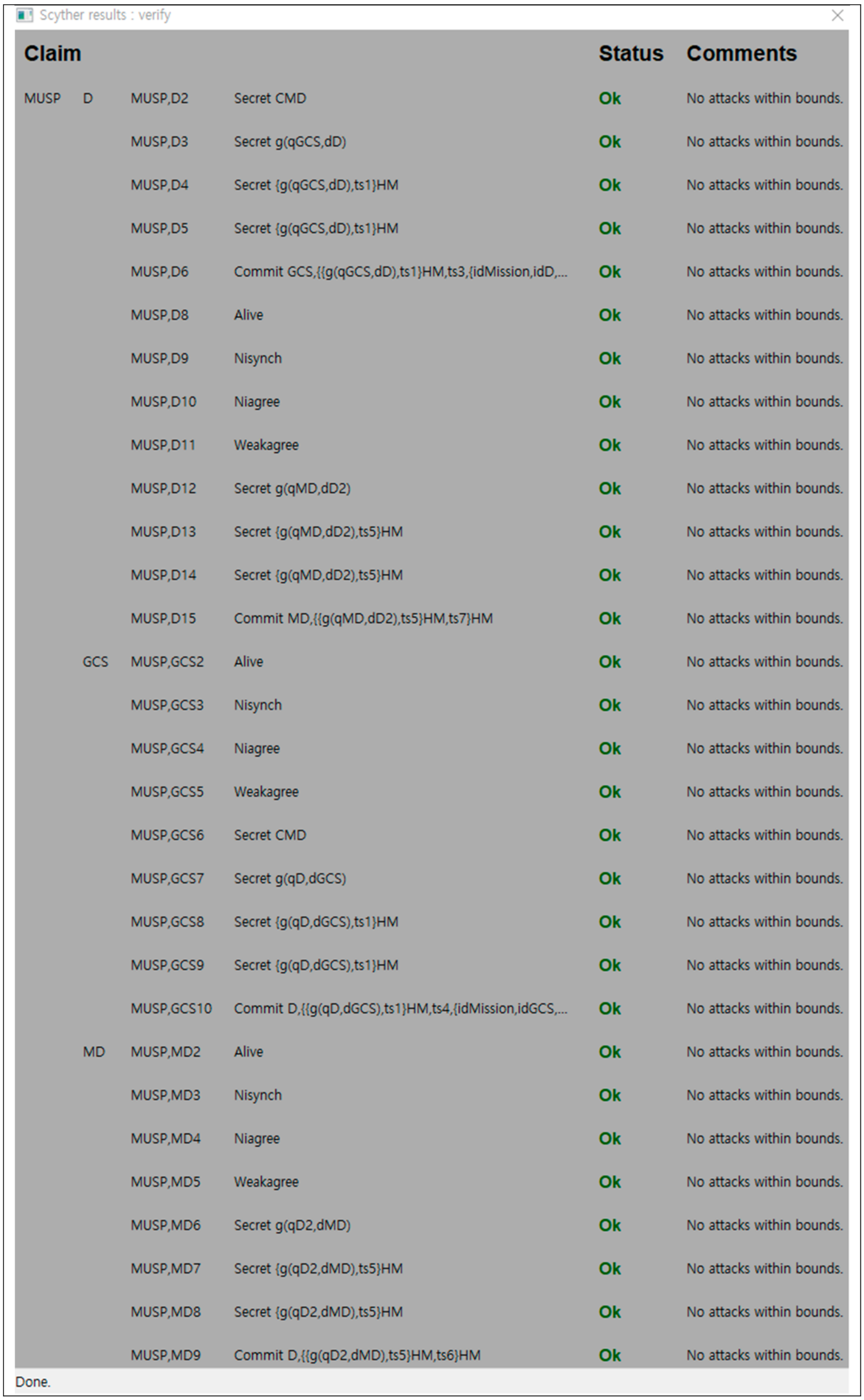
Sensors | Free Full-Text | Drone Secure Communication Protocol for Future Sensitive Applications in Military Zone | HTML
![PDF] Analysis and Verification of a Key Agreement Protocol over Cloud Computing Using Scyther Tool | Semantic Scholar PDF] Analysis and Verification of a Key Agreement Protocol over Cloud Computing Using Scyther Tool | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/df932f9db948e0e49c26a748ca2eec9d76e3c118/5-Figure3-1.png)
PDF] Analysis and Verification of a Key Agreement Protocol over Cloud Computing Using Scyther Tool | Semantic Scholar

Analysis and improvement of the Internet‐Draft IKEv3 protocol - Cheng - 2017 - International Journal of Communication Systems - Wiley Online Library

The results using 'verification claim' procedure in Scyther tool (see... | Download Scientific Diagram

A secure and robust elliptic curve cryptography‐based mutual authentication scheme for session initiation protocol - Nikooghadam - 2020 - SECURITY AND PRIVACY - Wiley Online Library

The results using 'verification claim' procedure in Scyther tool (see... | Download Scientific Diagram
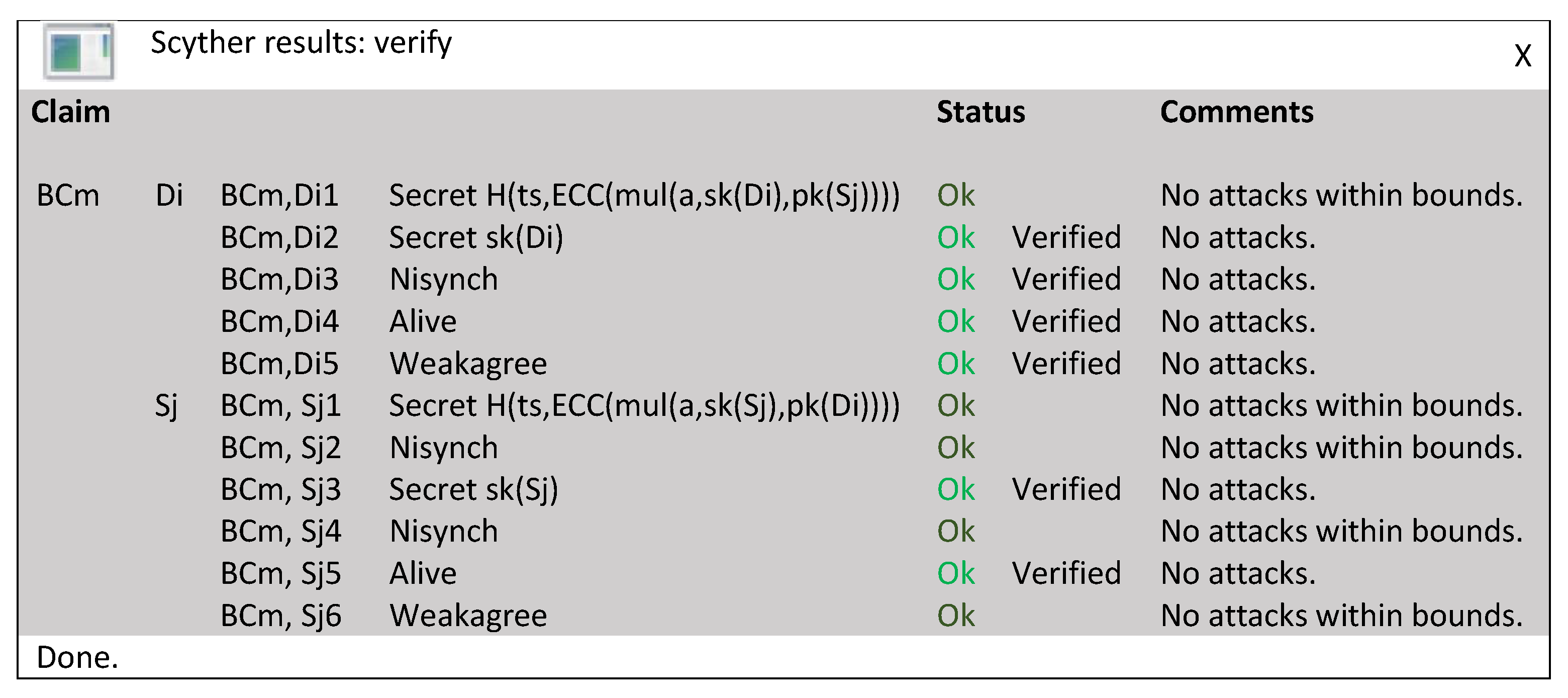
Mathematics | Free Full-Text | BCmECC: A Lightweight Blockchain-Based Authentication and Key Agreement Protocol for Internet of Things | HTML

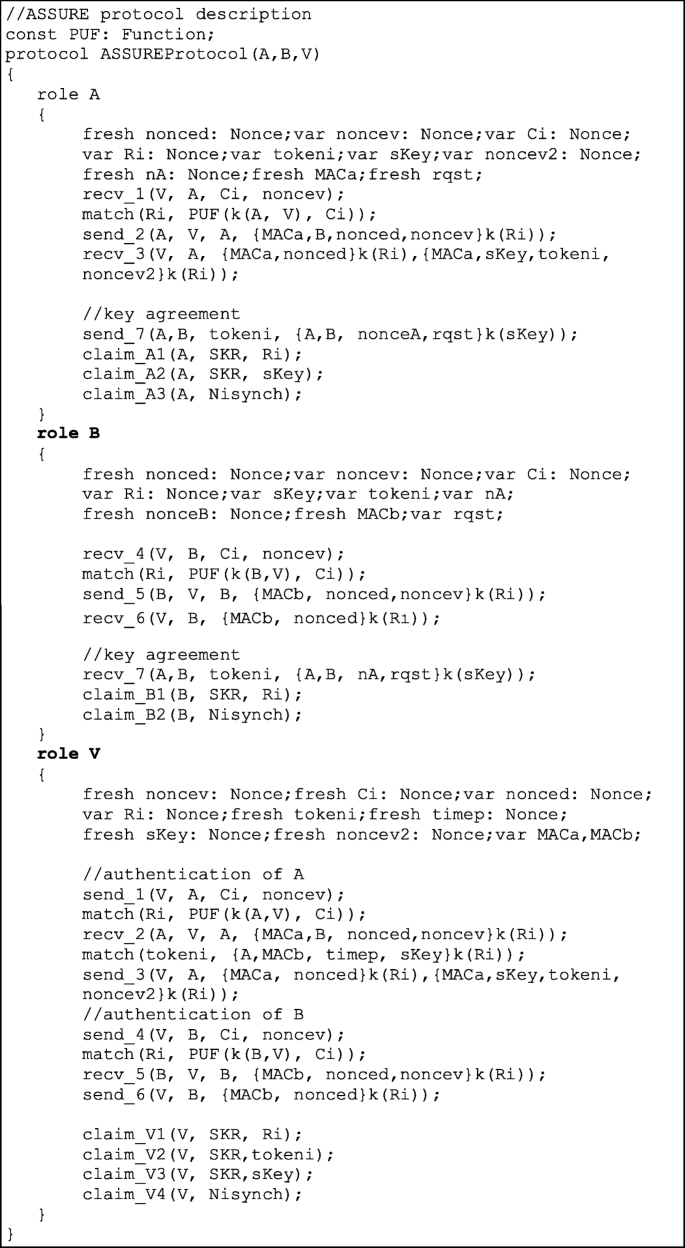
![PDF] Verifying Group Authentication Protocols by Scyther | Semantic Scholar PDF] Verifying Group Authentication Protocols by Scyther | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/afecefc52bb5c36f7b968eac7aaf7c24361b5813/10-Figure2-1.png)

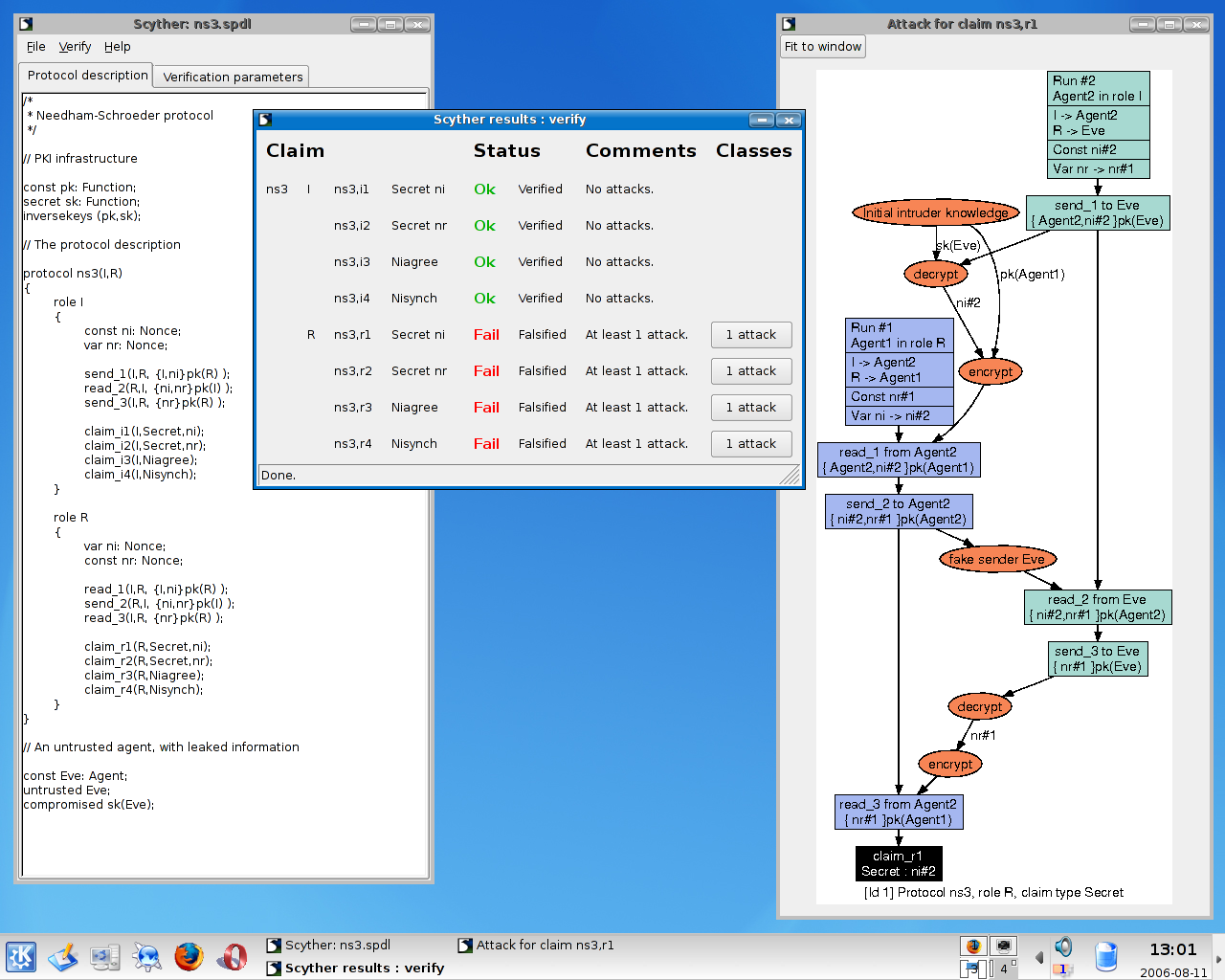


![PDF] Verifying Group Authentication Protocols by Scyther | Semantic Scholar PDF] Verifying Group Authentication Protocols by Scyther | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/afecefc52bb5c36f7b968eac7aaf7c24361b5813/12-Figure3-1.png)






