
Scyther (Formal Verification Tool) Installation on Windows #Scyther #Formalverification #Windows - YouTube

Security verification results of the proposed scheme using the Scyther tool | Download Scientific Diagram

Security verification results of the Khemissa et al.'s protocol using... | Download Scientific Diagram

PDF) Formal Verification of the Authentication and Voice Communication Protocol Security on Device X Using Scyther Tool
GitHub - binhnguyen1984/scyther-abstraction: The Scyther-abstraction Tool for the symbolic analysis of security protocols

scyther tool installation on windows. Scyther model checker installation on windows OS. Formal Verif - YouTube
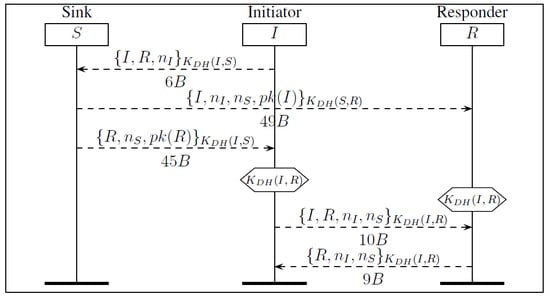

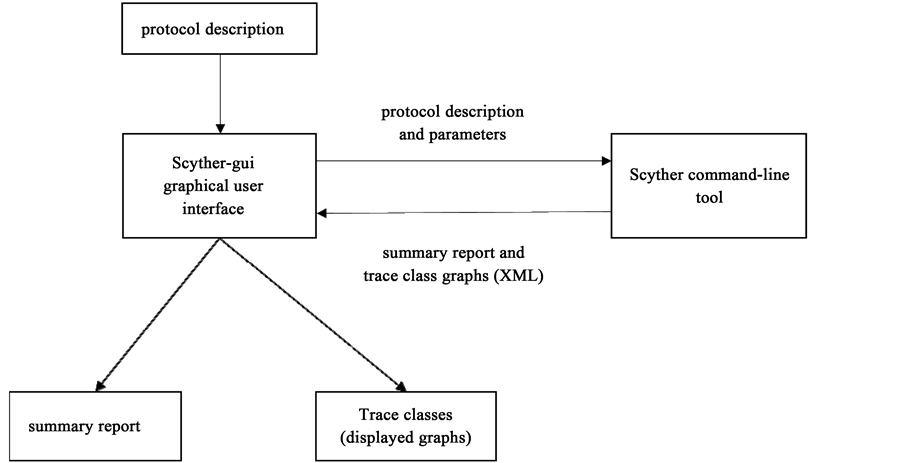

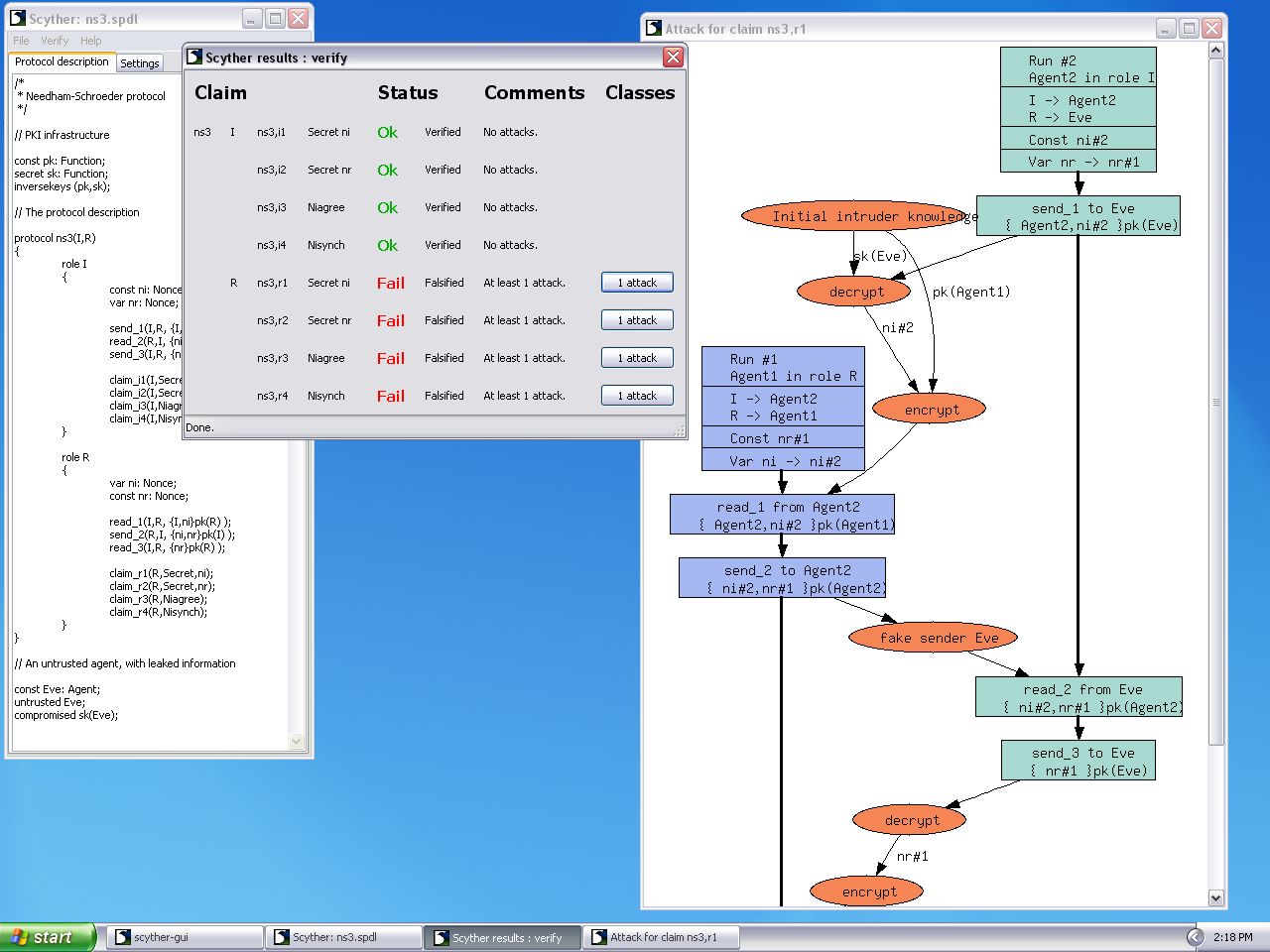


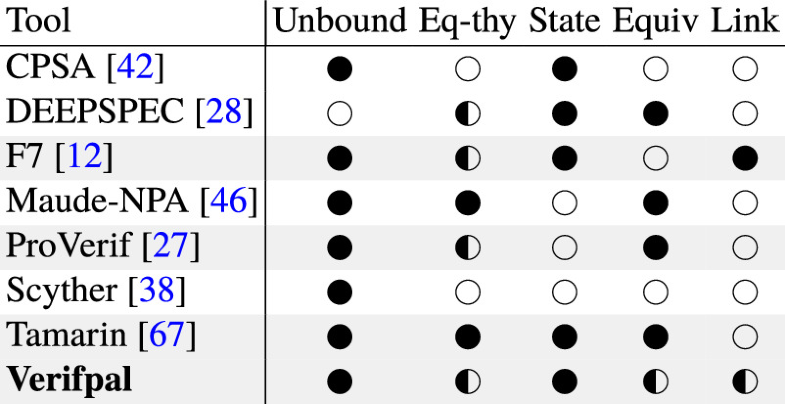





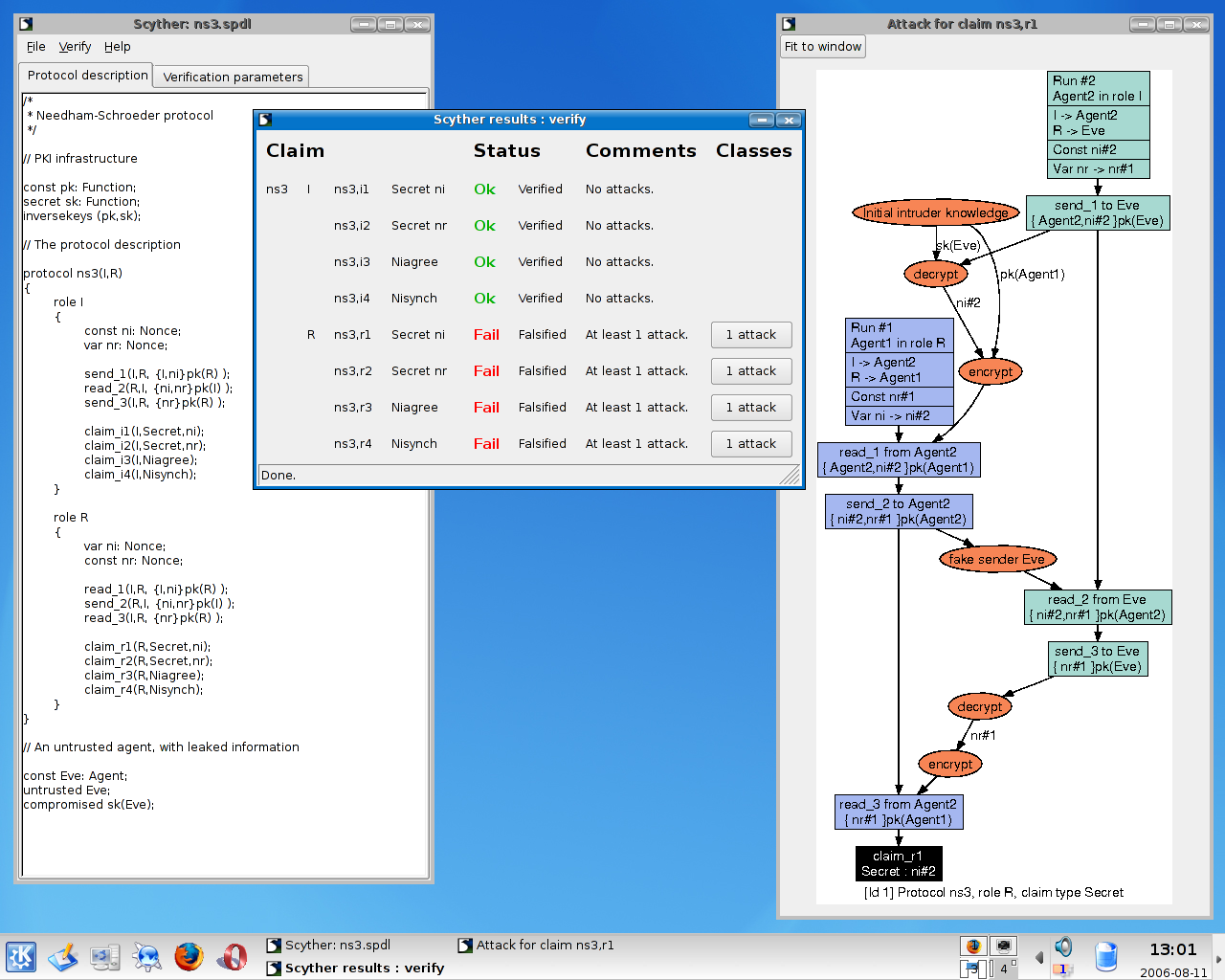
![Scyther Manual - [PDF Document] Scyther Manual - [PDF Document]](https://demo.staticloud.net/img/full/reader018/html5/20191105/55cf8f2a550346703b998e16/bg1.png)



